
NIS2 Directive Compliance Deadline
By October 17, 2024, relevant EU organizations must comply with the Network and Information Systems Directive 2 (NIS2) directive and publish…
Season simulator Why are there seasons?
Recently, I stumbled upon a fascinating project known as “The Nebraska Astronomy Applet Project.” It delves into intriguing questions such as…
iOS Privacy Settings Check List
Maximize Your Privacy and Battery Life: Essential iOS Settings to Consider 1. Optimize Location Services for Privacy and Battery Life To…
MySQL Error “file too short” when creating sys_exec function
I recently encountered an intriguing error message, “file too short” when attempting to elevate privileges on a Linux system through the…
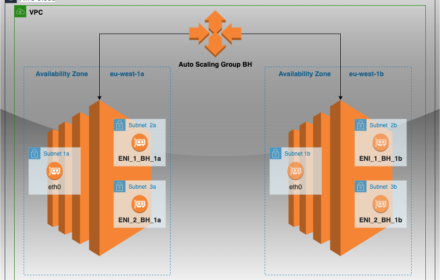
How To Attach Multiple ENIs To EC2 Instances Without Lambda
Creating a Launch Template in AWS of a single EC2 instance with multiple elastic network interfaces (ENIs) is quite straightforward. How…
Finding vulnerabilities with Windows Exploit Suggester – NG
Windows Exploit Suggester NG (WES-NG) is a tool based on the output of Windows’ systeminfo utility which provides the list of…
Configuring Ansible Dynamic Inventory aws_ec2 plugin
We already know how to connect to AWS instance using SSH over AWS SSM, so we are ready to go one…
Connecting to AWS EC2 instance using SSH over AWS SSM
It is very common that enterprise security policies don’t allow direct connections from corporate networks to EC2 instances over SSH. A…
The Linux Adventure: Finding Happiness Beyond Windows
Another work week begins, and as I open my laptop, I’m greeted by the familiar and frustrating sight: “Configuring Windows Updates,…
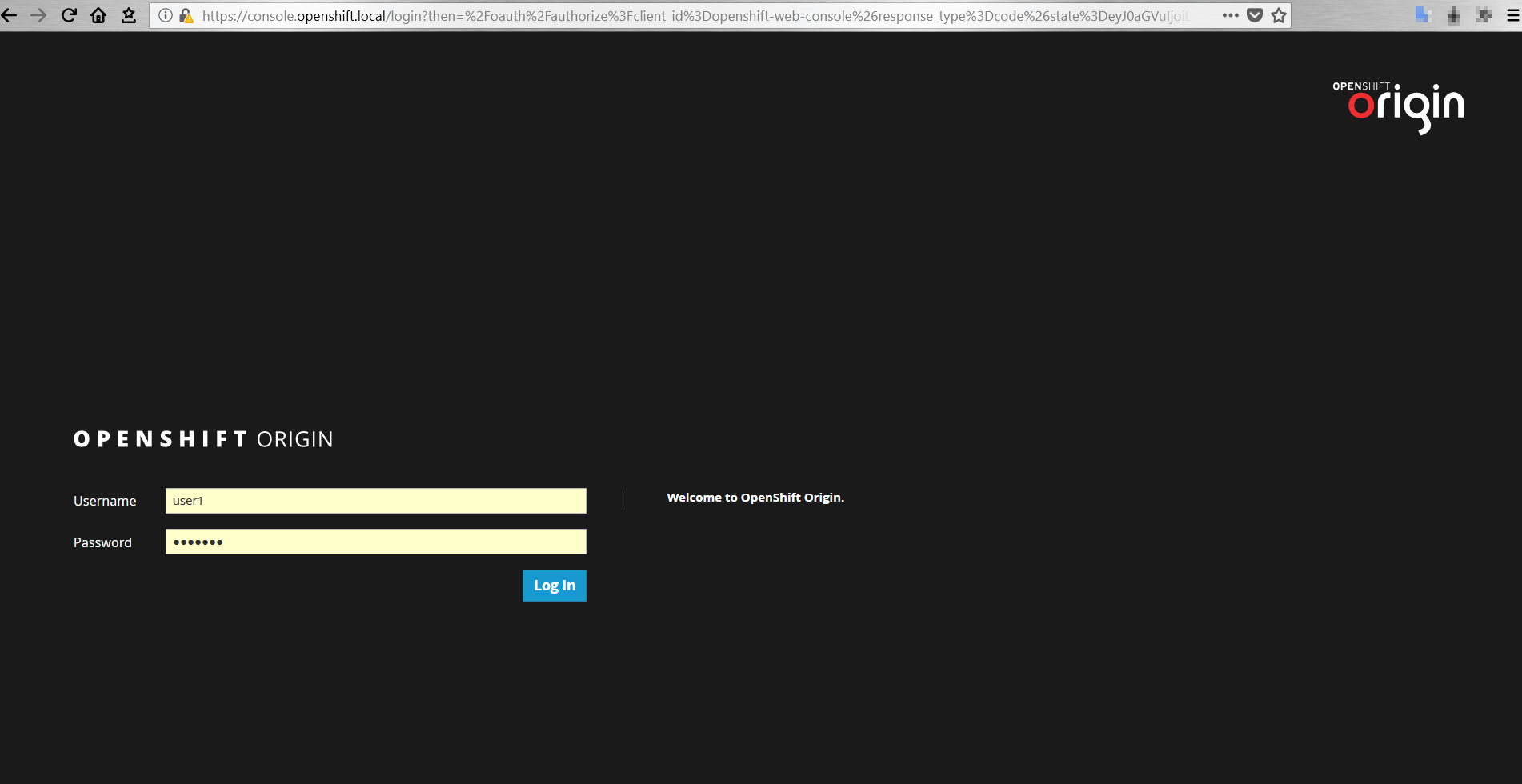
Installing OpenShift Origin in a Home Lab
We are going to demonstrate how quickly get us up and running with a “lightweight” OpenShift Origin environment in a virtual…