Connecting to AWS EC2 instance using SSH over AWS SSM
It is very common that enterprise security policies don’t allow direct connections from corporate networks to EC2 instances over SSH. A preferred and more secure way is using AWS Systems Manager. However, we can still connect to the EC2 instance using SSH over SSM.
What is AWS Systems Manager (SSM)? It is an AWS service that you can use to view and control your infrastructure on AWS. It works in a very similar way to ssh, allowing users to connect to ec2 instance as “ssm-user” the same way as over ssh as “ec2-user”. The connection can be established from a Linux terminal using AWS CLI or from AWS web console.
There are some basic prerequisites for SSM:
- AWS CLI tool is installed on a client machine (to use a terminal)
- a working connection to AWS account using AWS CLI
- SSM Agent is installed on EC2 instance
- ssh public key is assigned to EC2 instance
SSM Agent is preinstalled, by default, on the following Amazon Machine Images (AMIs):
- Windows Server
- Amazon Linux
- Ubuntu Server
Connecting to an EC2 instance is as simple as running the following commands:
$ export AWS_PROFILE=profile_name $ aws ssm start-session --target i-06exxxa5fxxxc03xx
Now, let’s configure SSH client to proxy connections to EC2 instances over ssm session.
We can proxy ssh connection over ssm the same way as can we proxy connections to remote servers via stepping stone servers, also known as bastion servers. To set this up we ad the following to ssh config file:
# edit ~/.ssh/config, add the following lines: host i-* mi-* 10. User ec2-user ProxyCommand sh -c "export AWS_PROFILE=<name>; aws ssm start-session --target %h --document-name AWS-StartSSHSession --parameters 'portNumber=%p'" IdentityFile ~/.ssh/aws-key.pem
That will ensure whenever we run ssh command and the target hostname starts with “i-” or “mi-” or “10.”, our connection will be proxied via ssm session.
For example:
$ $ ssh-add ~/.ssh/aws-ec2-private-key.pem $ ssh ec2-user@i-002d7e70587b0c355 or $ ssh -i ~/.ssh/aws-ec2-private-key.pem [email protected] or simply $ ssh i-002d7e70587b0c355
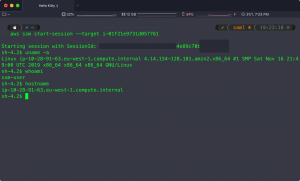
In the result we will connect to the EC2 instance:
$ ssh ec2-user@i-002d7e70587b0c355 Authorized uses only. All activity may be monitored and reported. Last login: Wed Nov 11 11:23:29 2019 from localhost [ec2-user@ip-10-12-82-123 ~]$ uname -a Linux ip-10-12-82-123.eu-west-8.compute.internal 4.14.133-113.112.amzn2.x86_64 #1 SMP Tue Jul 30 18:29:50 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
Having working SSH over SSM is very useful whenever there is a need for managing EC2 instances using Ansible playbooks. Ansible requires connection over ssh protocol. One of the typical scenarios is the migration of existing on-prem, Ansible managed infrastructure to AWS. There will be no need for rewriting existing playbooks, that will continue to work with EC2 instances running in the cloud.