cybersecurity

NIS2 Directive Compliance Deadline
By October 17, 2024, relevant EU organizations must comply with the Network and Information Systems Directive 2 (NIS2) directive and publish…
iOS Privacy Settings Check List
Maximize Your Privacy and Battery Life: Essential iOS Settings to Consider 1. Optimize Location Services for Privacy and Battery Life To…
MySQL Error “file too short” when creating sys_exec function
I recently encountered an intriguing error message, “file too short” when attempting to elevate privileges on a Linux system through the…
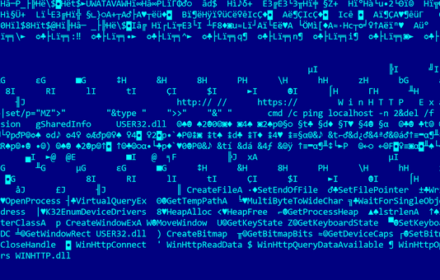
Finding vulnerabilities with Windows Exploit Suggester – NG
Windows Exploit Suggester NG (WES-NG) is a tool based on the output of Windows’ systeminfo utility which provides the list of…
Connecting to AWS EC2 instance using SSH over AWS SSM
It is very common that enterprise security policies don’t allow direct connections from corporate networks to EC2 instances over SSH. A…
Installing Sophos UTM 9 Firewall In Home Network
If you value the security and online well-being of your home network or the safety of your children, you may be…
A secure home network with a free Intrusion Detection System
Traditionally, households have accessed the internet through the use of ISP modems, which often come equipped with basic routers and Wi-Fi…