Configure SSL in WebLogic Server Domain
Quick guide on how to implement SSL in WebLogic Server domain. Custom Identity and Custom Trust with self-signed certificate.
First, let’s create custom directory to store self-signed certificate, custom keystore and custom trust store files:
mkdir -p /u01/app/oracle/config/domains/wls12c_domain/security/SSL
Modify input variables according to your requirements and run below script on WebLogic Server host. This script will automate entire procedure and does the following:
- create keystore
- create self-signed certificate
- export the server certificate
- create Trust Store
#Script: Generate Keystore
DOMAIN_HOME=/u01/app/oracle/config/domains/wls12c_domain
cd ${DOMAIN_HOME}/security/SSL
JDK_HOME="/bin"
ALIAS="zion"
DNAME="CN=example.local.net, OU=ZION Support, O=ZION Inc, L=Gotham, ST=StateOfMind, C=EU"
KEYPASS="password"
IDENTITY_JKS="identity.jks"
STOREPASS="password"
CERT_CER="cert.cer"
TRUST_JKS="trust.jks"
#create-keystore
echo "Creating keystore"
${JDK_HOME}/keytool -genkey -alias ${ALIAS} -keyalg RSA -keysize 2048 -sigalg SHA256withRSA -dname "${DNAME}" -keypass ${KEYPASS} -keystore ${IDENTITY_JKS} -storepass ${STOREPASS}
#Self Signing the Certificate
echo "Self Signing the Certificate"
${JDK_HOME}/keytool -selfcert -alias ${ALIAS} -dname "${DNAME}" -keypass ${KEYPASS} -keystore ${IDENTITY_JKS} -storepass ${STOREPASS}
#Exporting the Server certificate
echo "Exporting the Server certificate"
${JDK_HOME}/keytool -export -alias ${ALIAS} -file ${CERT_CER} -keystore ${IDENTITY_JKS} -storepass ${STOREPASS}
#Creating Trust Store
echo "Creating Trust Store"
${JDK_HOME}/keytool -import -alias ${ALIAS} -file ${CERT_CER} -keystore ${TRUST_JKS} -sigalg SHA256withRSA -storepass ${STOREPASS} -noprompt
echo ""
echo "Done"
echo ""
To check the content of the keystore
keytool -v -list -keystore identity.jks
Next, Login to Weblogic Server Admin Console, go to Servers and select the managed server you want to update.
- Go to Configuration -> Keystore tab
- Click the
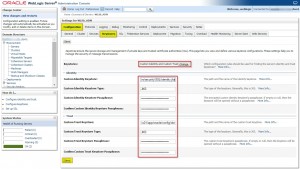
Changebutton under Keystore Configuration and selectCustom Identity and Custom Trust - For the Custom Identity Keystore, enter the path to identity.jks file, next type in Keystore type:
JKS - Enter your Custom Identity Keystore Passphrase as the password
- For the Custom Trust Keystore: enter the path to trust.jks file
- Keystore Type:
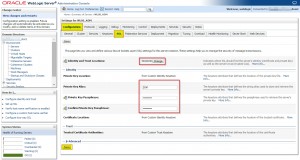
JKS.ClickSavebutton - Go to Configuration -> Keystore -> SSL tab
- Enter the server certificate key alias (in our example:
zion), and the keystore password - Click
Saveto apply the changes.
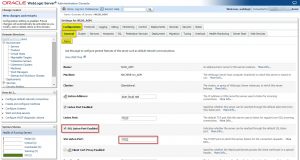
Finally go to Configuration -> General tab and enable managed server to be listening on SSL port. Save changes.
 You need to reboot WebLogic managed servers for the changes to take effect.
You need to reboot WebLogic managed servers for the changes to take effect.
Extra tip: You may like the following WLST script which will automate the WebLogic Server configuration part – WLS_configure_SSL
Cheers!!